Someone on our VDI team informed me that they were getting an error when trying to log into their VSCA:
“An error occurred during authentication.”
I started with the usual troubleshooting - did it work with my credentials? (No, it did not). Did it work in a private browser window, to rule out a caching issue? (No, it did not).
I tried logging in locally, but none of the accounts that should have worked, actually worked. So, before actually troubleshooting the issue, I had to break into the VCSA. Following the advice in Resetting root password in vCenter Server Appliance 6.5 / 6.7 / 7.x (2147144), I:
- took a snapshot (including memory) of the VCSA as currently configured
- Reboot the vCenter Server Appliance.
- After the VCSA Photon OS starts, press the e key to enter the GNU GRUB Edit Menu.
- Locate the line that begins with the word Linux, then appending these entries to the end of the line:
rw init=/bin/bash - Press F10 to continue booting. Ran the command
mount -o remount,rw / - In the Command prompt, enter the command passwd and provide a new root password (twice for confirmation):
passwd - Unmount the filesystem by running the umount command:
umount / - Reboot the vCenter Server Appliance via
reboot -f - Confirm that you can access the vCenter Server Appliance using the new root password.
At that point, I was finally in via CLI.
I then had to reset the password for administrator@vsphere.local. I followed the steps in How to unlock and reset SSO password in vSphere 6.x/7.x using the vdcadmintool (2146224) to use the /usr/lib/vmware-vmdir/bin/vdcadmintool tool for this.
A look in /var/log/vmware/vsphere-ui/logs/vsphere_client_virgo.log showed entries similar to this:
The SSL certificate does not match when connecting to the vCenter Single Sign-On.
com.vmware.vim.vmomi.client.exception.VlsiCertificateException: Server certificate chain is not trusted and thumnprint verification is not configured.
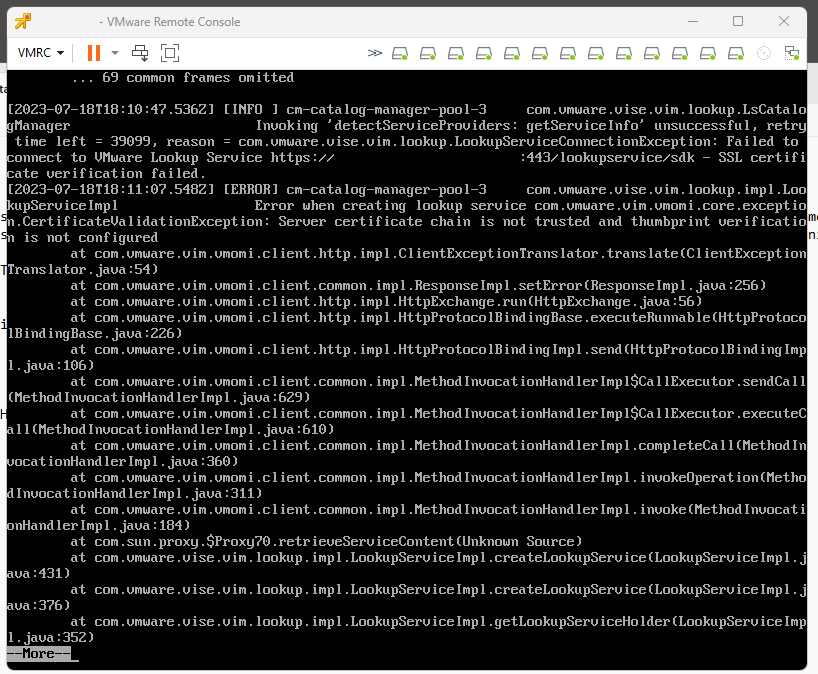
That confirmed that this was likely a certificate error. I started by checking the STS certificate, following the advice in Checking Expiration of STS Certificate on vCenter Servers (79248), but the STS certificate was valid until 2029.
I then looked at the other certificates by using check-trust-anchors -cml, which showed that the certificates had indeed expired 10 days ago:
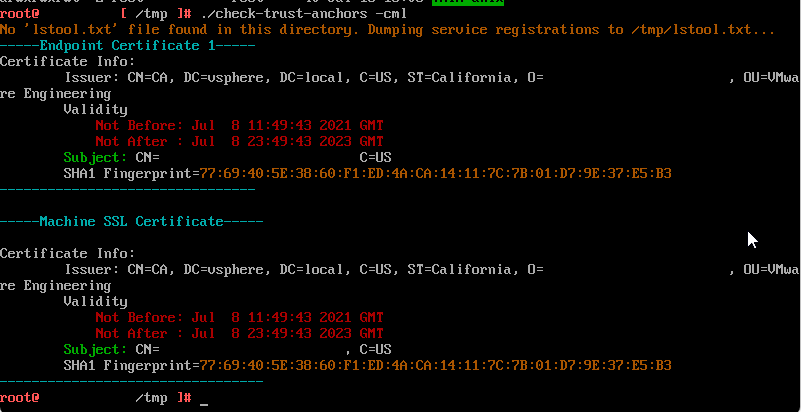
I followed the advice in How to regenerate vSphere 6.x, 7.x, and 8.0 certificates using self-signed VMCA (2112283) to generate a new certificate:
- Connect via. SSL or console
- Launch the vSphere 6.x Certificate Manager:
/usr/lib/vmware-vmca/bin/certificate-manager - Select Option 4 (Regenerate a new VMCA Root Certificate and replace all certificates)
- Type the administrator@vsphere.local password when prompted.
- Enter the appropriate values when prompted by the VMCA
- Confirm proceeding:
You are going to regenerate Root Certificate and all other certificates using VMCA. Continue operation : Option[Y/N] ? : YAfter 5 minutes, the operation completed and the new certificates were in place.
Refreshing the VCSA website allowed me to log in, and the VDI team confirmed that everything was working again. Hurrah!